Security Central: The NSA Gets Hacked, Expert Highlights SMB Cybersecurity Trends
Among the growing number of major organizations getting hacked these days, we can now add the National Security Agency (NSA) to the list. Well, sort of. This week, the NSA was reportedly targeted by a group of hackers who call themselves the Shadow Brokers.
August 19, 2016

Among the growing number of major organizations getting hacked these days, we can now add the National Security Agency (NSA) to the list. Well, sort of. This week, the NSA was reportedly targeted by a group of hackers who call themselves the Shadow Brokers. On Saturday, the “shady” crew released a series of files containing malware and attack code developed by the NSA-associated team, Equation Group. According to an article by Forbes, those tools have been used to launch cyber-attacks on other governments and private organizations globally over the last two decades.
According to Forbes, the Shadow Brokers released 60 percent of the files they claimed to have taken from the Equation Group. The hacker group said they would hold onto the rest of the data and would release it to the highest bidder in a Bitcoin auction. The demand? 1,000,000 Bitcoins, which is worth approximately $560 million. Only at that point will they release the rest of the information.
While most experts on the case are saying that the leak is legitimate, some are speculating that it’s an extremely believable and well-carried-out ruse. The reason for that challenge stems from the fact that the first Tweets from the hacker group were sent to various media outlets. Even still, sources are still calling the hack real.
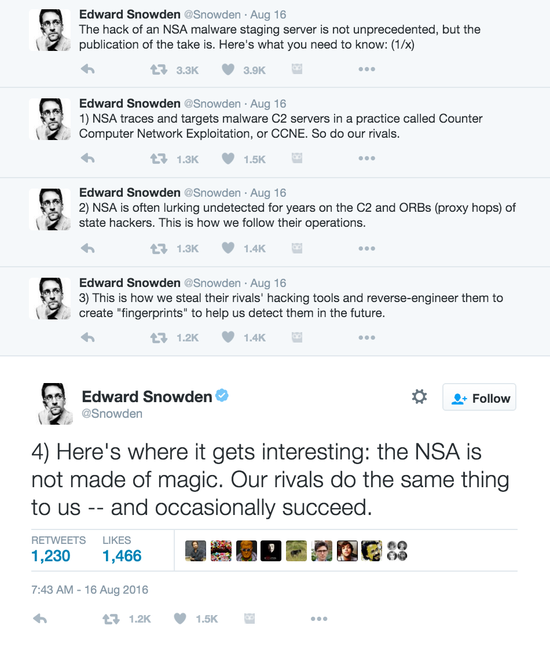
“The code in the dump seems legitimate, especially the Cisco exploits … and those exploits were not public before,” said founder of cybersecurity start-up Comae Technologies Matt Suiche. “The content seems legit.” The infamous Edward Snowden, former NSA contractor, even weighed in on the situation, saying in a tweet that the hacking of an “NSA malware staging server is not unprecedented, but the publication of the take is.”
Snowden went on to say that just as the NSA has the tools to hack into foreign governments, which it does, those governments in turn also hack the United States. “Here’s where it gets interesting: the NSA is not made of magic. Our rivals do the same thing to us — and occasionally succeed,” Snowden said. Snowden has since speculated that Russia is behind the hack.
While we’re on the topic of government organizations getting hacked, it was reported that Bill and Hillary Clinton’s charity, the Clinton Foundation, hired the security company FireEye to conduct a thorough inspection of its network after detecting possible hacking attempts. According to an article by Reuters on Wednesday, nothing has surfaced that would either prove or disprove that the organization was indeed breached, such as leaked files or information.
It is speculated that those allegedly responsible for the possible attack used the same tactics that were leveraged against the Democratic National Committee (DNC), a technique called “spear phishing.” The attackers appear to have sent foundation staffers bogus email attachments or links to websites containing malicious content. In a recent exchange with Fortune, Craig Minassian, the Clinton Foundation’s communications chief, mentioned that the Foundation has not discovered a compromise.
“What I told you before is still true,” he said, referencing a statement he made back in June in regards to the alleged breach of the foundation that occurred then. “We have no evidence Clinton Foundation systems were breached and have not been notified by law enforcement of an issue.”
Further, some experts are aiming blame for the supposed attacks at, you guessed it… Russia. The U.S. government has made no official claim regarding this allegation, but some experts and Democratic Party members are urging the Obama administration to do so. Jim Himes, a Democrat on the House of Representatives intelligence committee, said the United States should be viewed as a country not to be trifled with and should carry “a big stick” in the area of cybersecurity. “The U.S. government needs to be very clear, very direct, and hold these people accountable.”
Even without official blame being placed for this particular instance, the Democratic Congressional Campaign Committee held a closed-door meeting on Wednesday to address the continued and near-constant threat of attacks on the DNC and discuss best cybersecurity practices. Even though nothing has surfaced from this alleged attack, considering the fact that the DNC and other Democratic organizations have been successfully hacked a number of times before, the party is taking no chances. According to Fortune, officials fear more hacking attempts and potential data breaches could be on the way.
The political arena is certainly a hot-button issue these days and a prime target for hackers, but another space getting a lot of attention is the world of small and medium-size businesses. On Monday during the Channel Partners Evolution conference in Washington, D.C., CTO Mike Davis of detection and response company CounterTack shared that as large enterprises are becoming better and smarter at detecting and fending off attacks and breaches, cybercriminals are now turning their focus on small and medium-size organizations.
Taking out the smaller players who may not necessarily have the means for the high-profile defense tactics that large organizations do isn’t a surprising next move for hackers. Davis highlighted the devastating costs that a data breach could incur for a small business, saying that it will cost $300,000 on average. Setting up an effective defense structure and having experts on retainer to monitor systems for threats is nothing to sneeze at either, costing a minimum of $100,000, noted Davis.
A Business News Daily article published back in July emphasized the importance of cybersecurity for companies of all sizes, saying that small and medium-size businesses are just as much at risk for attacks as larger companies and are easier to penetrate due to less security. According to a report by Keeper Security and the Ponemon Institute, 50 percent of small businesses have been breached in the past 12 months.
An infographic by Towergate Insurance further emphasizes the holes in security and perception, showing that small businesses perpetually underestimate their risk level. 82 percent of small business owners are under the impression that they aren’t likely targets for attacks because they don’t have any assets valuable enough to be worth stealing.
Davis’s comments at the Channel Partners Evolution conference highlights this gap in awareness and education throughout the industry, and call to attention the increasing shift in hackers’ focus. Davis’s advice? Companies should regularly address, patch and update any security vulnerabilities. The majority of these network vulnerabilities “are two years old or more, while half of exploitations occur between 10 and 100 days after the vulnerable information is published,” Davis indicated.
No matter the scam or hacking attempt, or the area at which it’s aimed, all of these instances scream for proper training and awareness. It could be as simple as educating employees about phishing email scams or as complicated as efficiently beefing up security tactics to ward off hacks from foreign governments. Either way, there remains a lot to be done. As rep. Jim Himes puts it, the “stick” we carry not only needs to be larger, but more importantly, smarter and more effective.
About the Author(s)
You May Also Like


