How Ransomware Is Accelerating in the COVID-19 Era
Focus on cybersecurity to stop hackers from preying on people's fear of the coronavirus.

We all knew that a second wave was coming, just not quite when. Like a hurricane gathering in the distance, we could only wait for our fate.
Then it came. From July through September, new COVID-19 cases per day hovered between 200- and 300,000 worldwide. By mid-October, 400,000-plus per day was the norm. According to Google, on Oct. 28 we shattered our previous all-time high, with more than 550,000 new cases reported in only 24 hours.
Luckily, hospitals around the globe had prepared for this eventuality. Unfortunately, so had hackers.
On Oct. 29, in the midst of the planet’s worst disease outbreak in 100 years, two dozen U.S. hospitals and health care facilities were attacked. Hackers took over their computer systems, demanding tens and, in some cases, even hundreds of thousands of dollars in ransom.
The patients in those hospitals — laying in those beds, struggling to breathe, hooked up to machines — didn’t know that they were in the crosshairs of Russian cybercriminals.
Cybercrime Loves COVID
COVID-19 is a curse on the world, and a gift to cybercriminals. Last year saw record numbers of cyberattacks of all kinds, from phishing campaigns to brute force attacks. There’s been an onslaught of COVID-related malicious domain registrations-tens of thousands created every day. And there’s Zoom–bombing, which hardly even existed before March.
Even against all of this, ransomware has stood out. But it’s not the frequency so much as the severity of these attacks that has caused such an impact. Attackers have targeted highly sensitive corporations, government entities and, in particular, research labs and hospitals.

Doctors perform a surgery at Brno University Hospital in the Czech Republic. (Herrndorf image/Shutterstock)
Take, for example, Brno University Hospital. BUH is one of the Czech Republic’s leading sites for COVID-19 research. Around mid-March the virus was just starting to make hay in Europe so, suffice it to say, the hospital was as hectic and vulnerable as ever that month.
Peter Gramantik, a malware researcher, was a patient at the facility on March 13. Around 5 a.m. that day, a different kind of outbreak occurred. He told ZDNet what happened: “The hospital public announcement system started to repeat the message that all personnel should immediately shut down all computers due to ‘cybernetic security.’ This message was repeated like every 30 minutes.”
The entire building’s IT network had shut down. Two other BUH branches, the Children’s Hospital and the Maternity Hospital, also went down.
As it became clear that the problem wouldn’t go away quickly, doctors were forced to postpone urgent surgeries. Gramantik, himself, was sent home. Even worse: hospital staff began rerouting new, acute COVID-19 patients, directing them to a different nearby hospital.
A Ransomware Pandemic
What happened in Brno seemed utterly novel at the time, but in retrospect, it is far from unique. Hospitals and COVID-19 research centers worldwide have been hit weekly, even daily, since the start of the pandemic.
But it’s not just health care that’s been impacted, of course. Governments and …
… businesses have been going through the same thing.
Though corporate hacks tend not to put people in physical danger, their costs can be truly staggering. When Energias de Portugal was hit in April, its attackers demanded 9.9 million euros in ransom. For Telecom Argentina, in July, the price tag was $7.5 million. In October, German giant Software AG was held for $20 million. After negotiations failed, the hackers published financial documents, employee emails, ID scans and even employee passports to the dark web.
It’s spooky stories like these that motivate so many organizations to just pay up. In June, the city of Florence, Alabama, coughed up $250,000 dollars to its hackers. That same month, the University of California at San Francisco was hit. Because some of its encrypted data included important COVID-19 research, the university ceded, paying out an ungodly $1.14 million. (UCSF, of course, is largely supported by taxpayer funding. So, really, Californians paid $1.14 million to hackers.)
Why Ransomware, Why Now?
There are plenty of reasons why this pandemic has been so conducive to ransomware. We’re also on our devices more than we used to be. We’re using less-secure devices — personal computers over home networks instead of work computers over guarded corporate networks. And we’re using these devices to connect with others more often, introducing more attack paths for malware to spread. But these factors make us easy targets regardless of what attack vector hackers choose.
What makes ransomware, in particular, appealing during this pandemic is that we’ve become more reliant on our computers. Think of any company right now, and you’ll get the picture. All our business — all communications, all business functions — is currently being done over computer networks, so the potential cost of a shutdown is higher than ever. Where a ransomware attack in an office setting is a big deal, a ransomware attack in a remote work environment is game over. Similarly, although hospitals aren’t working remotely, they are more reliant than ever on their IT systems, with more patients needing more urgent attention at all hours of the day.
Actually, there’s an even more insidious reason criminals love COVID. It scares us.
Imagine being in Italy in March. The novel coronavirus has now spread to Europe, and your country is getting hit the hardest. People are dying in vastly overcrowded hospitals. Nurses must literally turn infected people away at the front door, and doctors are deciding who gets ventilators and who will die.
Amid all this, you receive an email:
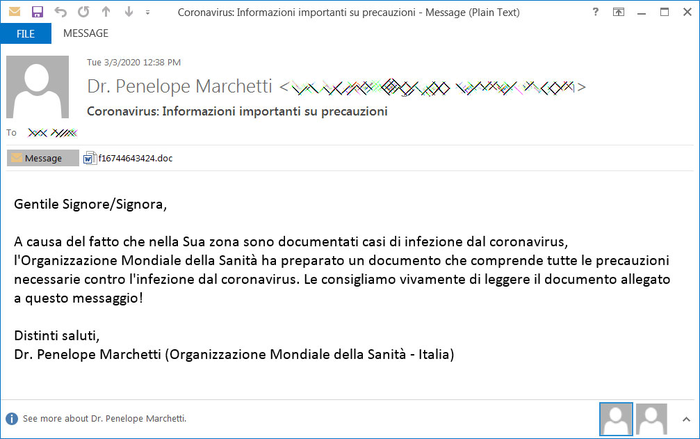
Courtesy: Diriga Technologies
Dear Sir / Madam,
Due to the fact that cases of coronavirus infection are documented in your area, the World Health Organization has prepared a document that includes all necessary precautions against coronavirus infection. We strongly recommend that you read the document attached to this message!
With best regards,
Dr. Penelope Marchetti (World Health Organization – Italy)
We knew so, so little about …
… the severe acute respiratory syndrome coronavirus 2, or SARS-CoV2 virus, in March. Everybody in Italy was suffering, and everybody around the world wanted answers, any scrap of information there was about the virus, its transmission or its treatment. How many of us could honestly say that, in such a state, we wouldn’t have clicked on that attached document?
Ransomware attacks usually start with a phishing email, and we’re three times as likely to click a COVID-19 phishing link than any other kind. It’s not because they’re more believable, but because we’re less discerning. Fear makes us irrational.
What to Do
Individuals and corporations have the capacity to deal with ransomware in a measured way. When an attack occurs we can at least try to take a breath, consider what data of ours is crucial and what isn’t, figure out whether we have backups, and decide whom we should call for help.
Hospitals usually don’t have this luxury. When two dozen U.S. health care facilities were held for ransom by Russian cybercriminals on Oct. 29, but also in plenty of other cases, the risks to human life made paying off even exorbitant ransoms worthwhile. It’s all part of a vicious cycle, where hospitals continually pay out so hackers repeatedly come back.
What we need now, more than ever before, is to make cybersecurity a forefront issue, to treat it as business-critical and as a public health risk. We should treat our digital workspaces like valuable investments, and give hospital IT networks as much care as the patients that rely on them.
Doing this will be important after the pandemic, but it’s especially urgent right now, because the mere existence of COVID-19 is, itself, a security threat. This pandemic has made us scared and vulnerable, and that’s exactly what our attackers want.
Ayesha Prakash is KELA‘s vice president of global channels, where she incorporates more than 15 years of experience across IT and cybersecurity industries. She has extensive experience driving global business development and marketing efforts in the cybersecurity space, previously holding positions such as head of global channels and partnerships and chief revenue officer at leading cyber intelligence firms. She was awarded a Top Gun 51 designation from Channel Partners Online. Ayesha serves on the board for the cybersecurity program for Pace University, Ithaca College and Rutgers University. She also is active in the Information Systems Audit and Control Association (ISACA), Women in Cyber (WiSys) and the Alliance of Channel Women. You may follow her on LinkedIn or @Intel_by_KELA on Twitter.
About the Author
You May Also Like


