All Tricks and No Treats When It Comes to Ransomware
As Halloween approaches, clowns aren’t the only unwelcome guests making headlines this holiday season. In the world of IT, malware is sinking its teeth into business data everywhere. Ransomware continues to hold business data hostage until companies pay up. Often, hackers demand payment within 72 hours or data will be deleted. Spooky.
October 17, 2016

Sponsored Content
As Halloween approaches, clowns aren’t the only unwelcome guests making headlines this holiday season. In the world of IT, malware is sinking its teeth into business data everywhere. Ransomware continues to hold business data hostage until companies pay up. Often, hackers demand payment within 72 hours or data will be deleted. Spooky.
So how can we defend the data from a ransomware encryption? In Q2 2016, Datto conducted a survey of 1,100 managed service providers (MSPs) to uncover the trends behind this creepy software. Below, I’ve highlighted some of the current hacker tricks that have been wildly successful when it comes to infecting systems.
Trick 1: Phishing
In Datto’s report, managed service providers ranked phishing emails as the No. 1 cause of ransomware attacks (see image below). Phishing scams typically target employees via email under the mask of someone a user works with or knows well. For example, a hacker may masquerade as a representative from the user’s bank and demand account login credentials for a site update. Users are familiar with the sender, so they often comply pretty quickly.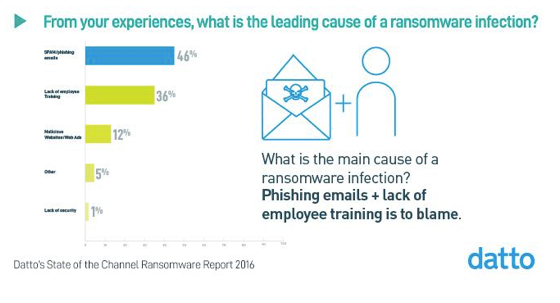
Trick 2: Unmasking the Hackers
Ransomware victims often never learn who the people are behind the hacks. That’s right: The masks rarely come off. Hackers are shielded behind their computer screens and seldom deal with repercussions of their actions. In fact, according to Datto’s report, less than 1 in 4 ransomware incidents are reported to authorities. And why would they? Currently, there is no guaranteed way to decrypt the data that is held hostage–not even the FBI can break today’s sophisticated ransomware code.
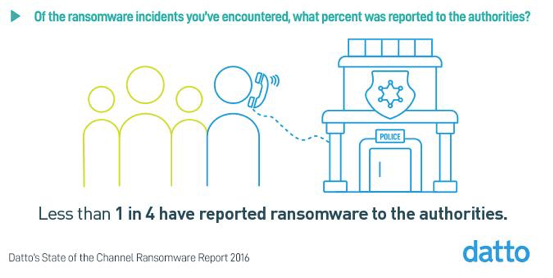
Trick 3: Payment Doesn’t Equal Data
Today’s cybercriminals are well aware of the toll they are taking on businesses. In fact, downtime from ransomware costs businesses in the United States an estimated $75B per year. That’s a lot of money! This is why many businesses simply pay up in order to avoid the costly downtime. But, unfortunately, paying the ransom in no way guarantees the data will be returned. In fact, of the 42% of MSPs who reported their end users had paid the ransom, 1 in 4 did so and still never recovered access to their data. This is largely why the FBI recommends victims do not pay up.
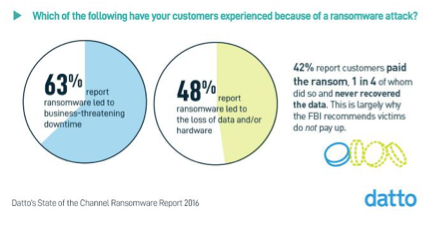
The hackers behind ransomware might have a few tricks that have gotten them this far, but we’ve caught on to their schemes. Of the MSPs we surveyed, nearly 100% of them were able to resolve ransomware attacks if they had a backup and disaster recovery solution in place for their end users. This makes sense as the U.S. Department of Homeland Security recommends backup and disaster recovery as the No. 1 protection for businesses against ransomware.
If you’re interested in learning more about the current state of ransomware and how Datto’s solution can ensure you never need worry about it, we’ve got a treat for you. Check out 2016 Datto’s State of the Channel Ransomware Report and get the facts!
Rob Rae is VP of Business Development, Datto.
Guest blogs such as this one are published monthly and are part of MSPmentor’s annual platinum sponsorship.
You May Also Like
