Phishing Trends for MSPs to Watch-Part I
The majority of today’s phishing attacks are becoming increasingly sophisticated--carefully crafted to obtain sensitive information from specific organizations, or even a particular person.
December 21, 2016

Sponsored Content
“Who would ever fall for that?” That’s what many customers think when they see a phishing attempt, since less advanced types of phishing often involve laughable requests with terrible grammar and spelling to lure victims. Most of these are sent to a large number of recipients in hopes that a few will respond, as even the smallest margin of return is a success. However, the majority of today’s phishing attacks are becoming increasingly sophisticated–carefully crafted to obtain sensitive information from specific organizations, or even a particular person.
Current phishing campaigns can affect just about any of your customers. And the losses from successful phishing attacks can be devastating. For example, the FBI recently reported that companies have lost billions of dollars in just the past few years from employees being tricked, often by phishing attacks, into making fraudulent wire transfer payments.1
Who Would Fall for It? Millions of People

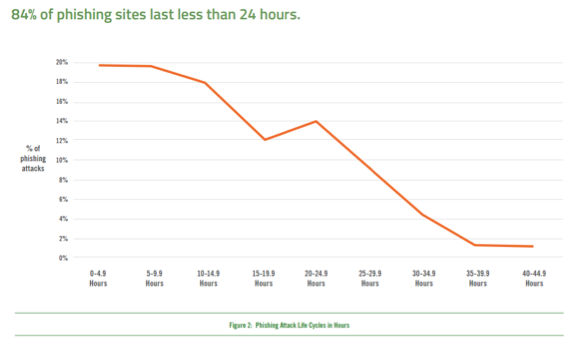
But why are phishing attacks so effective? 2016 Webroot research has given us some ideas about what’s going on. The most troubling trend in phishing is how much the life cycles for an attack have shortened. Back when a single phishing attack lasted for several weeks or months, organizations had time to block the email messages or websites the attack used to prevent more victims from falling prey.
Today, attackers have tools that automate the creation of fraudulent sites and the highly customized emails, ads, social media messages and other phishing content. Figure 2 shows phishing life cycles in hours based on a representative sample of over 800 phishing sites detected by Webroot in September and October 2016. The average life cycle was less than 15 hours. Twenty sites were online for less than an hour, with one lasting just 15 minutes, while the longest-lived site lasted less than two days (just 44 hours).
Highly Targeted and Short-Lived
The lifecycle of phishing domains and URLs has proven to be one of the next big challenges in cybersecurity, because traditional blacklists and domain-blocking services are almost useless in stopping today’s phishing attacks. Webroot analysis shows that almost 100 percent of the latest phishing URLs are using domains typically reserved for benign purposes. For example, an attacker may have compromised a single page on a web server and replaced that page’s content with a phishing page.
With so much change in phishing within the last year, it’s becoming harder and harder for MSPs to deal with the threat. As of the end of 2016, the only viable protection against the short-lived, highly targeted nature of phishing sites is cybersecurity that’s capable of blocking phishing attacks in real time.
Stay tuned for our second blog post on recent phishing trends, because we’ll be covering more data on the ways phishing sites disguise themselves and the top contenders for most-impersonated brands in the phishing world.
Read the entire Webroot Phishing Threat Trends Report and see what else Webroot research unveiled in 2016.
1FBI, Alert Number I-061416-PSA (2016, June 14). https://www.ic3.gov/media/2016/160614.aspx
Guest blogs such as this one are published monthly and are part of MSPmentor’s annual platinum sponsorship.
You May Also Like
