Shadow IT: Out of the Shadows and into the Cloud
Here’s how MSPs can tackle shadow IT as a part of a security services offering.
July 31, 2020
Sponsored by Kaspersky
‘I’ve sent it to you in cloud disk
‘We don’t use cloud disks here’
‘No worries. I’ll send you a link’
Shadow IT–the use of IT systems and applications without the knowledge or approval of the business–has grown exponentially. With the adoption of cloud-based applications and services, it’s just so easy for users to reach out for their own preferred tool to do the job.
Someone outside the business sends you a file in cloud disk like Box, Dropbox, Google Drive or something similar. Then, when you need to send that file to someone inside the business, so you install that application and tell them to use it, too. Next thing you know, everybody’s using cloud disk messengers, third-party mail and social networks in the office. But nobody’s told IT (naturally, or they might get told to stop), so whoever’s tasked with enforcing IT policy–whether it’s you or your client–has no idea where the business’s valuable and potentially sensitive data is being stored in the cloud. And how, or even if, it’s protected.
What you don’t know about, you can’t control, or patch, or protect. So shadow IT becomes a “blind spot��” in terms of your clients’ security. And, with Gartner studies finding that shadow IT can represent as high as 30% to 40% of spending on IT, it’s perhaps less of a blind spot and more of a black hole.
So how do you, as an MSP, tackle shadow IT as a part of your security services offering?
Discovery
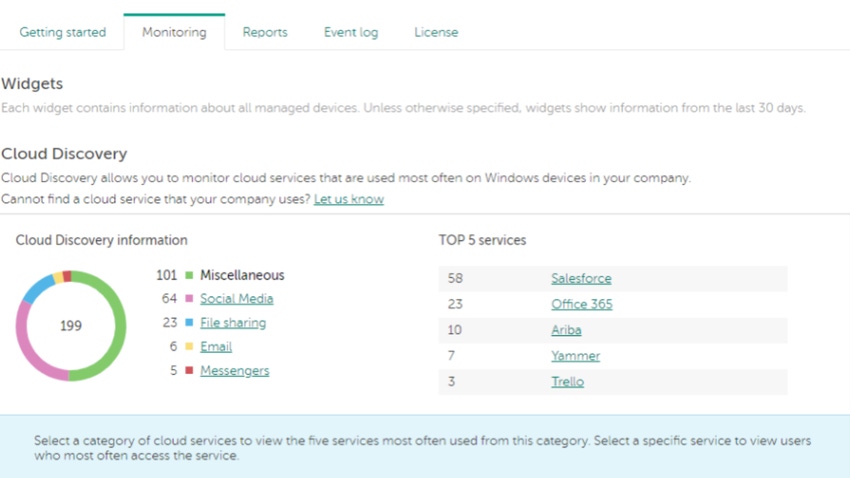
The first task is clearly to find out exactly what unapproved cloud services are actually at work in your customer’s business. For those with deep pockets and plenty of time, firewalls and CASBs (cloud access security brokers) can be used to do this. For the rest of us, applications specifically dedicated to this task (our own Cloud Discovery is just one of them) can provide a clear, straightforward, ongoing picture of what software is in use, how often it’s accessed and by which users.
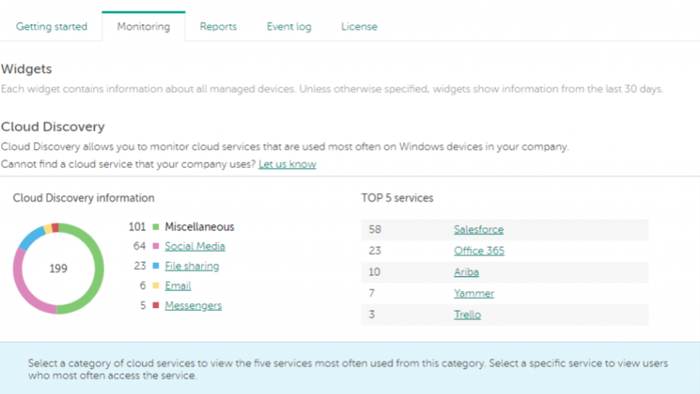
Shadow IT Discovery in Action
Once you know what you have, you can start taking a look at the associated risks and potential damage to be faced. Are we talking mainly about potential data breaches or time-wasting social media usage? Now is a good time for you as an MSP to get a report on the table for your client’s CEO or HR Management or both.
Control
Having sat down with your client and looked at what’s really happening, it’s time to talk about preventing the creep of shadow IT by controlling and blocking applications. You’ll want to think about what to block and for which users. There will be VIP users with much wider permissions and those whose roles require access to specific applications that may be unavailable to others. You may decide to ban access to some applications only during core office hours, while blocking others entirely.
Replacement
Having limited or blocked access to unauthorised applications, it’s critical to provide appropriate replacements so people can work effectively. You may take a look around the market researching for the best cloud collaboration tools that fit your business needs. And one of the criteria to keep in mind is for that new cloud-based software to meet your cybersecurity requirements and data protection compliance.
Multiple Security Services
And, at this point, I’d like to put in a word for one of Kaspersky’s own security offerings. Aside from award-winning endpoint protection and granular controls, Kaspersky Endpoint Security Cloud incorporates a number of special features and applications with managed services providers in mind, including Cloud Discovery, plus Kaspersky Security for Microsoft Office 365 (which can also be purchased as a stand-alone product). The current mass-migration to Microsoft Office 365 provides the perfect opportunity to tackle shadow IT full-on. So, through a single product purchase, you can offer your clients a range of security services, including:
Shadow IT discovery and management
Security for MS Office 365 (anti-phishing, antimalware) and for major Office apps: Exchange Online, OneDrive, SharePoint Online and Teams
Patch management and vulnerability assessment
Encryption management
And, with everything incorporated into one license and administered through a single console, you’ll find bringing your clients safely out of the shadows and into the cloud can involve you as their MSP with less time, as well as less expenditure, than you may have predicted!
This guest blog is part of a Channel Futures sponsorship.
Read more about:
MSPsAbout the Author(s)
You May Also Like


