5 Ways to Help Your Customers Avert Ransomware Attacks
Properly safeguarding against ransomware strikes has never been more critical.
October 15, 2021
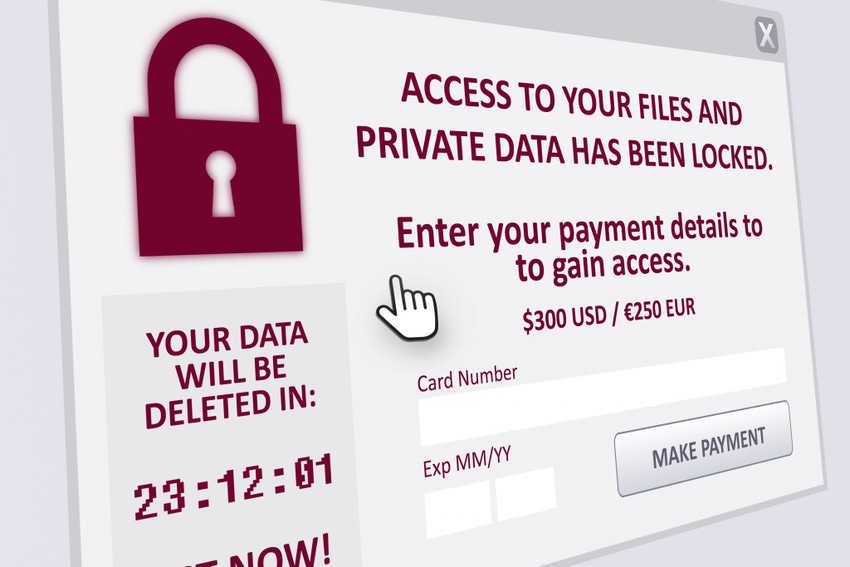
Ransomware attacks represent an escalating threat for every organization, regardless of size or sector. A form of malware that is designed to block system access until a fee is paid, ransomware can be especially dangerous to small and midsize organizations that often lack the security budgets, IT personnel and expertise of their enterprise-level counterparts.
Properly safeguarding against ransomware strikes has never been more critical. In 2020 alone, the prevalence of attacks in the United States skyrocketed by 109%, which experts attribute to the massive influx of home-based employees resulting from the COVID-19 pandemic. In this new hyper-distributed IT environment, threats are everywhere–and costs are steep. Ransomware is estimated to cost businesses more than $75 billion a year, with the average price tag of ransomware-related downtime ringing in at $8,500 per hour.
With increasingly savvy and opportunistic attackers out in full force, your customers need every possible advantage to ensure their organization is properly protected. Here are five ways you can help:
Encourage education.
Information security awareness training for employees can go a long way toward helping to identify and combat increasingly sophisticated ransomware threats. It is important for customers to recognize that the most common vector for ransomware to infect business systems is through phishing attacks, where hackers attempt to gather personal information like usernames and passwords through fraudulent websites or emails meant to impersonate trusted individuals or organizations.
Don’t leave power infrastructure vulnerable.
A business’ cybersecurity health is only as strong as its weakest device, so make sure that your customers secure uninterruptible power systems (UPSs) and other critical power infrastructure. While many companies may not recognize power infrastructure as a potential point of vulnerability, cybercriminals certainly do. Case in point: In 2013, attackers used a vulnerability in the HVAC unit of a major retailer to steal data on 40 million debit and credit cards belonging to customers. The hack underscored the importance of safeguarding UPS, power distribution and cooling systems against these determined threat actors. As thieves continually strive to overcome the cybersecurity mitigations businesses are putting in place, organizations must ensure that there is no point of access for malicious hackers through their connectivity products. For this reason, it is important to deploy network and connectivity devices that meet the UL 2900-1 cybersecurity standard.
Use an air gap.
Organizations may also wish to deploy an “air gapped computer,” a security measure to ensure that a computer network is physically isolated from unsecured networks, including the internet and local area networks. The goal of a physical air gap is to secure sensitive information so cyber attackers can’t get their hands on it. One manufacturer’s UPS software has even proven to be a cost-effective, highly viable cyber protection solution for cybersecurity. Working with a UPS or PDU, the software provides a unique way to automate common IT tasks and schedule air gaps to minimize the attack surface area of the infrastructure.
Encourage them to update their business continuity plan.
Successful organizations not only utilize the previously discussed mitigations to prevent becoming a victim of ransomware, but also have a comprehensive business continuity plan in place. The first step is to make sure that files are regularly backed up. In some cases, this simple process will allow victims to recover their data at no cost. Because ransomware attackers will sometimes try to coerce a company to pay the ransom by threatening to publicly release sensitive information, organizations should always encrypt their data to prevent attackers from gaining this type of leverage. And because it is also possible for ransomware attackers to encrypt or destroy backups, it is important to maintain a copy in a separate location that is isolated from their network.
Engage partners who are experienced with cybersecurity.
Working with vendors who understand the need for a multi-pronged cybersecurity approach can go a long way toward keeping your customers safe. To minimize the threat of operational downtime, data loss, and impacts on lifecycle costs and brand reputation, customers need suppliers who are willing and able to provide evidence that the products they sell comply with industry cybersecurity standards. Look for manufacturers that not only have established cybersecurity processes and innovative technologies, but also collaborate with standards leaders such as UL (Underwriters Laboratories) to establish measurable cybersecurity criteria for network-connected power management products and systems. In addition, the optimal partner will be continuously working to discover new ways to protect products and systems against cyberattack while helping customers deploy and maintain secure solutions.
This guest blog is part of a Channel Futures sponsorship.
Read more about:
VARs/SIsAbout the Author(s)
You May Also Like



