And socially constructed attacks continue to thrive.


James Anderson
Ransomware accounted for 39 percent of malware-related data breaches last year, according to a new study by Verizon.
The continued rise of ransomware was one of the many findings of the 11th annual Verizon Data Breach Investigations Report (DBIR). The 68-page study examined more than 2,200 data breaches and more than 53,000 security incidents. The findings reveal an increasingly common and elegant form of ransomware.
David Hylender, senior network analyst and principal with Verizon, tells Channel Partners that ransomware began appearing in the DBIR case load approximately three years ago. The number doubled in 2016 and doubled again in 2017 to 39 percent of malware breaches.
“That’s getting pretty close to half,” Hylender said. “That’s a big deal. And in addition to becoming more common, it is becoming somewhat more advanced.”
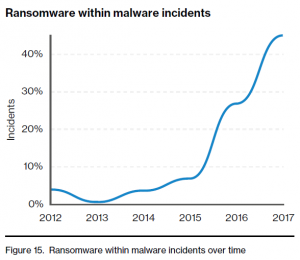
Source: Verizon DBIR
The report concluded that ransomware incidents are more increasingly going into “business critical” systems like servers and databases. The monetary demands of cybercriminals are, in turn, growing.
Health Care an Outlier
While ransomware affects every industry, Hylender notes that it accounts for 85 percent of malware in health care. He cited strict compliance measures like HIPAA and HITECH that subject health organizations to scrutiny similar to that of government agencies.
“They have to disclose things that other organizations may not have to report publicly,” he said. “Therefore, the number goes up.”
This vertical yielded different results in multiple categories compared to its counterparts. In addition to reporting a higher proportion of ransomware, health care was the only industry in which more incidents came from the inside (56 percent) than from the outside.
The study called human error one of the major factors for the prevalence of insider threats. Bryan Sartin, Verizon’s executive director, security professional services, said businesses must better educate their employees about cyber-related crime.
“Employees should be a business’ first line of defense, rather than the weakest link in the security chain. Ongoing training and education programs are essential,” Sartin said. “It only takes one person to click on a phishing email to expose an entire organization.”
Outside/Inside
Health care’s insider-threat problem was a major contrast to the rest of the overall study, in which Verizon found that outsiders perpetrated 73 percent of breaches.
The conclusions of the study disagree with other reports that say …
… careless or belligerent employees are the most common threat actors.
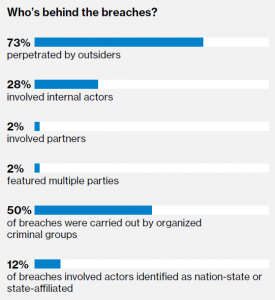
Source: Verizon DBIR
“While it’s true that an insider – a rogue employee for instance – can do a lot of damage if they decide to go the dark side as it were, it’s much less likely to happen than you are to be targeted by an external attacker,” Hylender said.
The Human Factor
Social attacks where criminals prey on human gullibility accounted for 1,450 incidents and 381 disclosures of data.
Phishing and financial pretext continue to be popular modes of attack. Cybercriminals looking for employee wage and tax details have scammed human-resources departments in multiple industries. Education, public agencies and health care were hardest hit with these social breaches.
“An attacker calls up, pretends to be an executive – usually a CFO type – and says, ‘Hey, I’ll need the tax-related data for all the employees in this sector here,'” Hylender said.
The bad guys often conduct their deception using a spoof email address – perhaps adding or subtracting a single letter from the expected address – but occasionally criminals use a hacked email address. Hylender says it’s common for the threat actor to delve into the hacked email archive in order to learn and mimic the writing style of the executive.
One of the main targets is a W-2 tax form that allows the thief to file taxes and receive a refund. Verizon found that this type of “financial pretexting” rose from 70 incidents in year 2016 to 170 in 2017.
“The scams are very very honed to get a particular thing, in this case tax-related documents to score cash from,” Hylender said. “Those have been extremely lucrative for attackers.”
Happy #DBIR day everybody! Obviously we are rather biased, but we are quite excited about the release of the 11th report. Thanks to all parties that contributed this year!
— The DBIR (@VZDBIR) April 10, 2018
The Scourge of DDoS
Verizon countered the claim that DDoS (distributed denial of service) is often a distraction for another type of attack.
“We don’t see a lot of that, contrary to what we’ve been reading in the headlines. We’re not saying that doesn’t happen, but we don’t see it much in our data set. It’s DoS for DoS’ sake,” Hylender said.
The report concluded that only one breach contained an instance of DoS, but the breach actually helped launch a DDoS, according to Verizon.
“In fact, we’ve never had a year with more than single-digit breaches in the denial-of-service pattern,” the DBIR wrote. “Like the aliens, they may be out there, but we aren’t seeing them.”
The lengthy report is available of Verizon’s website. The 2017 DBIR showed that SMB victims and espionage motives are rising factors in data breaches. We compiled a list of 12 common data breach scenarios and their causes.
Read more about:
AgentsAbout the Author(s)
You May Also Like


