It's a preview of the upcoming GRC Conference.
July 31, 2019

Security in cloud services has been viewed with skepticism and hailed as more secure than anything on-premises. In any case, lawyers continue to warn cloud customers that they will always be liable for data breaches.
Through it all, security providers have layered protections to add security in the cloud. But few know where the line is between the responsibilities of cloud security service providers and those of the companies that use them.
Dr. Sarbari Gupta, president and CEO of Electrosoft, will present “Who Is Responsible for the Security of Cloud-Based Information Systems?” at the 2019 Governance, Risk and Control (GRC) Conference, jointly presented by ISACA and The Institute of Internal Auditors, Aug. 12-14, 2019, in Ft. Lauderdale, Florida.

Electrosoft’s Sarbari Gupta
We asked Dr. Gupta to shed some light on the issue of responsibility for cloud security ahead of her presentation.
Channel Futures’ MSSP Insider: Adoption of cloud services does not imply full delegation of security responsibility. Where is the line (or where should it be) between the cloud providers’ security responsibilities and the cloud customers’ (organizations) security responsibilities?
Sarbari Gupta: The line that separates the responsibility of the cloud service provider (CSP) and the cloud customer depends on the type of cloud services acquired – such as infrastructure as a service, platform as a service or software as a service – and the layers of the IT stack that the customer implements themselves. My graphic (below) explains this further.
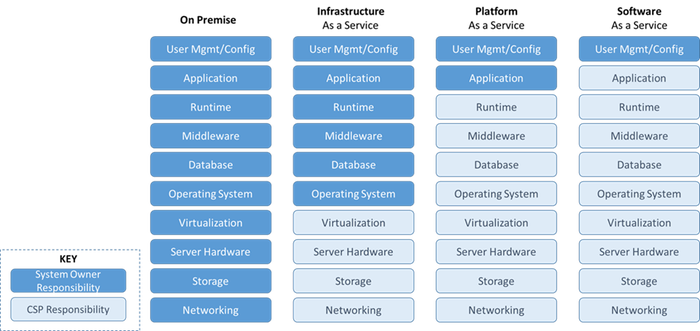 CFMI: You mention in your presentation a means for analyzing cloud service offerings to discover the cloud system owner (CSO)’s retained security responsibility. Please explain.
CFMI: You mention in your presentation a means for analyzing cloud service offerings to discover the cloud system owner (CSO)’s retained security responsibility. Please explain.
SG: To perform this analysis, the cloud customer needs to review the details of the security controls implemented by the CSP – using their FedRAMP package – against the full set of security controls required to be implemented by the cloud customer. Any gaps identified need to be filled by the cloud customer. This analysis is complex as well as laborious. I am proposing an approach that makes this analysis more manageable.
CFMI: Do you have any guidance or tips for partners or MSSPs on how to configure and complement security controls provided by cloud services to manage organizational security risk?
SG: MSSPs can make it easier for the U.S. federal cloud customer by providing the customer with their own analysis of the security controls and security control enhancements from NIST SP 800-53 that the cloud customer needs to implement themselves based on whether the target cloud system is to be categorized as FISMA LOW, MODERATE or HIGH impact. The cloud customer can then use this information to make an informed decision on their own retained security responsibility if they use that particular CSP solution.
CFMI: Any other tips for partners or MSSPs?
SG: The analysis described above can be performed once by the CSP/MSSP and can save countless hours of time for their customers as well as minimize customer risks. The CSP can tout this as a market discriminator!
If you would like to learn more, Dr. Gupta’s presentation is part of Track 3 at the conference, scheduled for Monday, Aug. 12, 11:30 a.m.-12:30 p.m. ET.
Read more about:
MSPsAbout the Author(s)
You May Also Like


