Countering threats to customers is best achieved with a staged approach to security services.
February 17, 2021
Sponsored by Kaspersky
Offering customers a portfolio of high-end corporate cybersecurity services may seem daunting, but it doesn’t have to be. Security vendors are constantly developing new technologies and solutions to deal with the latest and most advanced threats, yet all these technologies and solutions aren’t necessarily right for you, right now. The smart money is on taking a staged approach to security services, gradually scaling your portfolio to meet your customers’ needs and your own growth.
Countering threats to customers by providing managed security services is best achieved with a three-stage approach. This strategy lets you expand your cybersecurity portfolio at your own pace, without significant upfront investment. And with the right solutions, you don’t have to become an instant security guru, and it won’t take up much of your and your team’s time, either.
Although there is some overlap, each stage addresses a different threat category, and there are very clear ways to deal with the threats. Let’s take a look at this staged approach to security services.
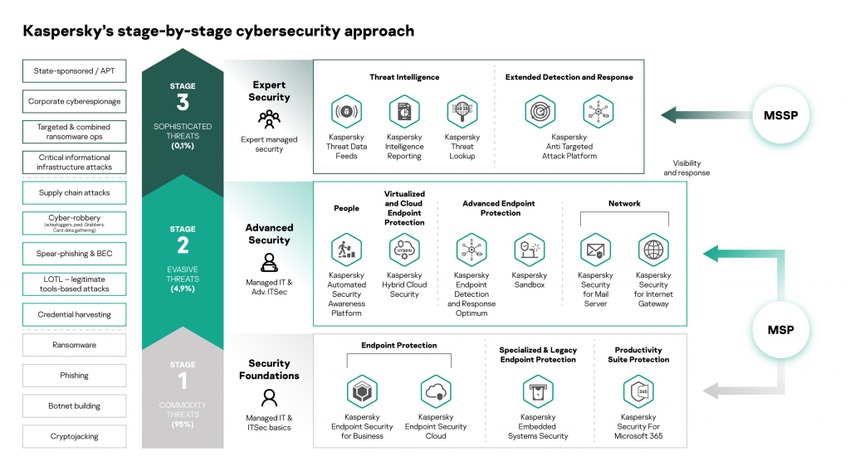
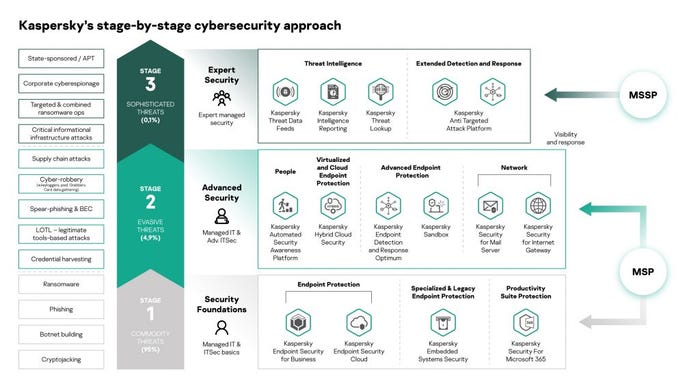
Stage 1: Commodity Threats
Commodity threats account for almost 95% of attacks, and include phishing attacks, ransomware, botnet building and crypto-jacking, data theft, and exploitation of vulnerabilities. They target the low-hanging fruit of businesses of every size.
Stage 1 threats begin with an attack on a single device and its user. It may end there, or it may just be the starting point to a wider attack. These attacks can be mitigated with a multi-layered EPP platform that provides the following capabilities:
Systems hardening with web, application and device controls
Encryption: Both full disk encryption (FDE) and file level encryption (FLE)
Anti-ransomware
Mail security
Vulnerability scanning and automated patch management.
Whether the platform is cloud-based or on-premises, the most important thing is that it delivers full protection against commodity threats while acting as a strong foundation from which to build up your practice.
Stage 2: Evasive Threats
Most of the other 5% of threats use evasive techniques that have been designed to evade the anti-malware components of EPP platforms. These include LOTL (living-off-the-land) attacks, spear-phishing and BEC (business email compromise), credentials harvesting, supply chain attacks and cyber-robbery.
For stage 2 threats, you’d want to deliver the following:
Endpoint detection and response (EDR)
Sandbox
Mail gateway and web gateway protection
Hybrid cloud security
Although you’ll need a higher level of security expertise here, you should also be able to rely on automated systems using machine learning technology to do most of the heavy lifting.
Stage 3: Sophisticated Threats
Stage 3 threats are sophisticated threats that may be custom-built, use seriously cutting-edge tech, and involve a lot of planning, complexity, time and patience on the part of the attacker (because the potential rewards are so great). We’re looking at things like state-sponsored attacks, APTs (advanced persistent threats), corporate cyber-espionage, large-scale targeted and combined ransomware operations, and attacks on critical infrastructures.
Tackling stage 3 threats requires a specific toolkit and cybersecurity expertise to provide:
Extended EDR (XDR)
Threat Intelligence
A private security network
Skills and awareness training
Access to external guidance and support.
By the time you’re offering these stage 3 services, you’re already a full-fledged managed security services provider. You have invested in training and advanced tools, and you have significant threat intelligence resources at your fingertips.
An organic three-stage approach is effective not only for you, but also for your customers. Providing a strong endpoint security foundation–then building and extending in scope as a business grows and diversifies as threats change–is the most efficient and cost-centric strategy. And when this staged approach to security services is supported by the right partner, the sky’s the limit.
Talk to Kaspersky to see if we can help you grow your security practice with a proven staged approach.
This guest blog is part of a Channel Futures sponsorship.
Read more about:
MSPsAbout the Author(s)
You May Also Like


