In today’s threat environment, security teams and managed security service providers, both large and small, need to incorporate active threat management into their security strategies and portfolios.
January 24, 2018
Sponsored Content
As an MSSP, protecting endpoints is a critical service offering. In that context, it is important to understand how endpoint protection solutions have evolved and what is necessary to protect against advanced threats.
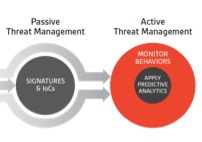
As threats evolve, it is no longer enough to provide only passive solutions. The current threat environment demands active threat management. Solutions like antivirus and next-gen AV are important components of any security strategy. However, they are passive threat management solutions. They scan files on disk against signatures and machine learning models to detect and prevent malware attacks. Their vendors are engaged in a never-ending game of cat and mouse with cybercriminals who continuously devise new malware variants to penetrate these solutions. AV and next-gen AV do not capture fileless attacks.
In today’s threat environment, security teams and managed security service providers, both large and small, need to incorporate active threat management into their security strategies and portfolios. They need to look to new detection and response solutions based on dynamic behavior monitoring and predictive analytics.
In order to understand emerging active threat management solutions, it is useful to look at the evolution of endpoint protection technologies.

The Evolution of Threat Detection Technologies
Antivirus. Antivirus is the first step in endpoint protection. Antivirus scans for malicious files using signatures. However, hackers understand antivirus techniques and continuously create new variants to bypass them. Antivirus vendors struggle to keep up. Antivirus is still relevant because it catches about 60% of today’s malware. However, it is ineffective because it is backward looking and not effective at catching 49% of today’s threats–fileless attacks.
Next-gen antivirus. Next-gen antivirus extends threat coverage with machine learning. Vendors continuously analyze malware samples and build models that scan and parse files, and then match features to detect new malware. Next-gen AV needs to keep machine learning models up-to-date. It doesn’t catch fileless attacks.
Application containerization. Application containerization is a limited solution for browsers or applications like MS Office. It monitors applications in a sandbox. If it detects a malicious event it will remediate it. It works off signatures and white listing. Application containerization effectiveness is limited to what’s going on in the sandbox.
Threat intelligence. Threat intelligence provides the next step and is the staple of legacy EDR solutions that rely primarily on incidents of compromise (IoCs). IoCs are signature-like. They look at OS events, filenames, command-and-control hosts and more, extrapolating a pattern that indicates malicious activity. IoCs need to be continuously updated to be effective. Threat intelligence is also backward looking.
Signatures. Machine Learning and IoCs are static technologies. The endpoint solutions that rely on them are engaged in a never-ending cat-and-mouse game to keep pace with today’s threats. They are ineffective at detecting new malware and fileless threats. They are post-breach solutions. They can’t discover threats until they carry out their behaviors.
Behavior-based. The first technology that is effective against fileless malware is behavior-based solutions that understand the threats themselves to provide protection without prior knowledge of the attack. Many EDR, or endpoint detection and response, solutions claim to behavior-based. True behavior-based solutions look for techniques that hackers use to carry out attacks. They look at processes, network connections, file and registry changes, and the pattern of those activities. Behavior-based solutions are effective because they don’t look at files or rely on threat intelligence.
In-memory threat detection. Advanced EDR solutions are evolving to predictive. Malware must run in memory to carry out and attack. In-memory threat detection looks at processes running in-memory and reverse engineers them to identify malicious behaviors and what the attack is trying to do. It is the most reliable technology for detecting new malware, fileless, and insider attacks.
Today’s Solution: Predictive EDR
An emerging class of predictive EDR solutions expand on traditional signature-based solutions by adding behavior-based and in-memory threat detection capabilities. This is the most reliable technology for detecting new malware and fileless attacks. It enables organizations to detect the most threats, without relying on signatures or IoCs, and provides the insight behind accurate and actionable predictive analytics. It detects suspicious behavior that other threat detection technologies can’t. It is the only solution that predicts what these behaviors can do. It empowers security teams to adopt more agile and proactive threat management strategies to prevent attacks, and should be the cornerstone of any managed detection and response (MDR) service offering.
Thom VanHorn is Senior Director Marketing, CounterTack.
This guest blog is part of a Channel Futures sponsorship.
You May Also Like
