Just this month, at an RSA session, Synack Research and Development Director Patrick Wardle was asked when ransomware for Mac OS X would arrive. His response was almost prophetic. “I’m actually really surprised we haven’t seen a bunch already,” he said. “There’s a lot of naive Mac users out there that are infecting themselves [with malware].”
March 25, 2016
By Cisco Umbrella Guest Blog
 Just this month, at an RSA session, Synack Research and Development Director Patrick Wardle was asked when ransomware for Mac OS X would arrive. Wardle is a former NSA employee, and has developed tools for detecting and blocking malware activity in OS X. His response to the question was almost prophetic.
Just this month, at an RSA session, Synack Research and Development Director Patrick Wardle was asked when ransomware for Mac OS X would arrive. Wardle is a former NSA employee, and has developed tools for detecting and blocking malware activity in OS X. His response to the question was almost prophetic.
“I’m actually really surprised we haven’t seen a bunch already,” he said. “There’s a lot of naive Mac users out there that are infecting themselves [with malware].” Technically speaking, he added, there’s no reason Mac ransomware doesn’t exist already. Adware has started popping up on the market, which is just as difficult–meaning not difficult at all–to develop.
Then, not even a week following Wardle’s RSA session, a version of crypto ransomware–possibly the first case–appeared. Dubbed KeRanger, and discovered by Palo Alto Networks, the ransomware version used a legitimate developer signature on a legitimate application called Transmission, an app used for downloading torrents.
In a previous RSA session–and at other conferences–Wardle demonstrated how crafting malware for the operating system is trivial, and how easy it is to bypass the safeguards Apple has put in place. These include Gatekeeper, the sandbox feature for applications. KeRanger seems to be a perfect case study in exactly how that works: a legitimate developer signature used to turn a benign application malicious, completely bypassing OS X’s built-in security.
This new development was not a disaster scenario, as Transmission developers issued a quick update and Apple revoked the abused developer signature in hours. Additionally, it appears the malware was caught in some cases by OS X’s built-in quarantine feature, as some Transmission forum users reported. KeRanger could be, however, an indication of something more drastic coming.
Ransomware Market Saturation
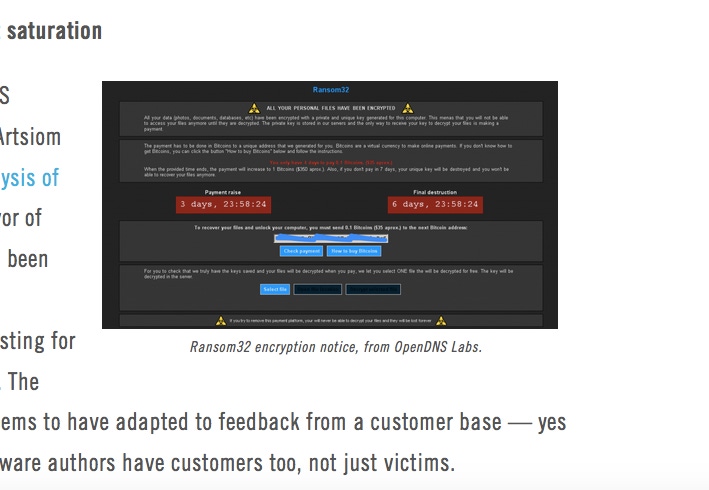
Just recently, OpenDNS Security Researcher Artsiom Holub published analysis of Ransom32. It’s a flavor of ransomware that has been around since at least January, but is interesting for a couple key reasons.
The first is the variant seems to have adapted to feedback from a customer base. Yes, ransomware and malware authors have customers, not just victims.
From Holub’s analysis:“The very first client was about 22 MB. The current are 1.06 MB and 3.31 MB. This indicates that the ransomware author listens to his customers. Decreasing the size and redesigning the package makes it a lot easier to use for malicious purposes.”
The author’s adaption to stay competitive and viable is also a reminder that ransomware exists in a competitive marketplace, where the most effective tools get the most business.
The second interesting note is the ransomware version is built on Node.js, a cross-platform JavaScript environment. Because it’s built on the Node.js platform, it could be translated to Mac OS X or Linux, which might mean it’s only a matter of time. And true to form, KeRanger was found to be a Linux infection reconfigured for OS X.
Ransomware, and malware in general, has not been the calamity it has been for Windows, largely because attackers are not yet focusing on OS X, and also because Apple’s app development process and requirements are more involved to keep applications secure. But, as TrustedSec CEO David Kennedy said in an interview with Slate, the marketplace for Windows malware and ransomware is competitive and may be turning saturated. If it becomes too saturated, or if Mac adoption continues its increase, more attackers might target OS X users to increase their profit.
A Bad Network Neighborhood
OpenDNS CTO Dan Hubbard and his team used the IPs and domain information to explore the network infrastructure for KeRanger and found what was probably expected.
Hubbard’s analysis shows the network neighborhood for KeRanger holds all sorts of unsavory sites, including drug sales, malware instruction sites and carding forums. It was also discovered that the attackers were using the Tor network, an increasingly trendy method hackers are using to decrease the chances of detection and tracking.
A Confusing Protection Game Plan
The advice for protection against ransomware is scattered and mostly a list of security best practices.
Kaspersky and other security firms have developed decryption codes for some variants of ransomware. But, as Holub’s article shows, the ransomware market is a competitive one, which means variants change often and new flavors appear regularly.
The only consistent advisory message from experts in ransomware protection is to back up files to the cloud. Attacks can render local backups useless, as they can also encrypt the backup files. This was reportedly one of KeRanger’s goals.
Backing up unfortunately does not prevent downtime, as it can be a large effort to restore thousands of endpoints if an attack hits a company’s entire network. As an example, a Hollywood hospital recently decided it was more efficient to pay the $17,000 ransom than it would have been to eradicate the infection and restore backups.
Wardle also suggests Block Block for Macs, a tool he developed himself that can detect if an application is exhibiting persistent behavior, like automatically launching after reboot. While this is normal behavior for some legitimate applications, it’s also a tip off to malicious applications, especially if they are unsigned.
Because of the security flaws in OS X, and the lack of a direct and easy way to protect them against attack, ransomware could become a pressing liability for both enterprises and individual users in 2016. In other words, the current reprieve from crippled machines, antivirus patching, and the moral dilemma of paying up or losing files may soon be at an end.
To learn more about ransomware, consider joining the upcoming webinar discussion between OpenDNS and Cisco’s AMP team taking place March 30 at 10 a.m.
See more at: https://blog.opendns.com/2016/03/10/17123/#sthash.fRBHYHFc.dpuf
Owen Lystrup is Marketing Content Manager for OpenDNS. He carries seven years of IT experience, including work in the security operations team for a Fortune 500 company. Guest blogs such as this one are published monthly and are part of MSPmentor’s annual platinum sponsorship.
Author: Owen Lystrup
Owen Lystrup is Marketing Content Manager for OpenDNS. He carries seven years of IT experience, including work in the security operations team for a Fortune 500 company.
– See more at: https://blog.opendns.com/author/owen-lystrup/#sthash.CeFp2KIB.dpuf
You May Also Like
