Here's a look at some cybersecurity issues every InfoSec specialist should be aware of in the coming months of 2018.
August 9, 2018

Sponsored by AT&T Cybersecurity
People around the world are becoming increasingly connected with smart devices. Sending and receiving massive amounts of data back and forth, we rely on the transfer and storage of data on a daily basis. Hackers and cyber attackers know this and know how to steal data for their profit. Your job as an information security specialist is to defend your company’s data, implementing preventative and protective measures and monitoring your data and systems.
With the increasing amount of data businesses and its customers are producing comes an increasing number of people maliciously trying to obtain it. In 2017, we saw increases in ransomware attacks, financial fraud and massive data breaches. It was a busy year for security practitioners, and 2018 has been and will be no different, with new global regulations, redesigned threats to new devices and ways to combat those threats.
Let’s take look at some cybersecurity issues every InfoSec specialist should be aware of as we move through the latter half of 2018.
Upcoming Requirements of the GDPR
The General Data Protection Regulation is the European Union’s way of protecting its citizens’ data by holding organizations and companies accountable in practices of security personnel in regards to sensitive information. As of May 25 of this year, companies risk severe fines if they are not in compliance with the GDPR data protection rules. In an effort to minimize the damage done during data breaches, GDPR rules determine how you and your company obtain and secure data, as well as how you notify users of a breach.
Under the GDPR, companies will rely on their IT security specialists to:
Be given explicit consent when obtaining customer data.
Be clear and upfront with customers in how they’ll obtain this data in language that is accessible and easy to understand.
Comply with data protection officers who will inventory data in the EU, including outside company data that pertains to goods and services held within the EU.
In the event of a breach, notify the public within 72 hours or be penalized.
The EU isn’t the only geography implementing privacy measures for its citizens. Australia implemented privacy regulations recently, as well.
The Liabilities of IoT
In a day and age where humans are increasingly integrating the internet into their day-to-day lives, we have no choice but to submerge ourselves in the internet of things (IoT). This includes the business world, as well. Mobile devices have become a necessity, and a network of connected smartphones, tablets and other smart devices has made it considerably easier for businesses to access information from the internet and communicate. It also has made it considerably easier for hackers to get their hands on the same information–which is, in turn, making it harder and harder on the InfoSec practitioner.
For usability purposes, nearly everything can be connected to Wi-Fi. A company’s smart coffee pot can be connected to an iPhone for a convenient cup of joe. However, there is data being transmitted and stored on networks that may or may not be secure. To make things worse, as companies implement more apps for their smart TVs or toasters, these networks are getting flooded with information, making it harder for you to track something so small. The graph below by Kroll Ontrack describes the steadily climbing rate of devices connected to the internet as opposed to actual internet users:
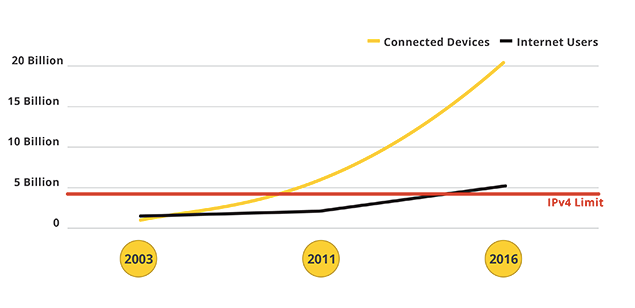
On one hand, it’s difficult to build proper security measures into most of these simple, often hastily manufactured, devices to maintain a competitive edge while also focusing on consumer safety. It’s nearly impossible to track and keep tabs on one toaster in a whole network–a double-pronged vulnerability that attackers are more than capable of exploiting. InfoSec practitioners will have their hands full tracking and building defenses for the susceptibilities of increasing IoT devices.
Data Protection & Cryptography
Despite an annoying recent trend for “crypto” to be used when referring to cryptocurrency, it normally refers to cryptography. As an information security specialist, you should know that cryptography is a standard in network security. It is the process of scrambling your company data to render it incomprehensible to people who are not intended to see it by way of encryption and unscrambling it for the people meant to see it after decryption. Cryptography, however is not without its flaws.
Cryptography works mainly in one of two ways, but the concept is the same. Your company’s data gets encrypted by a key into scrambled data, which is then transferred and decrypted back into the original data. In the case of symmetric-key encryption, the keys used to encrypt and decrypt your data use the same algorithm to code and decode your information. Asymmetric encryption adds another layer, as it requires a pair of keys in which a private key encrypts your data and is decoded by a public key. Cryptography can perhaps best be understood by a graphic:
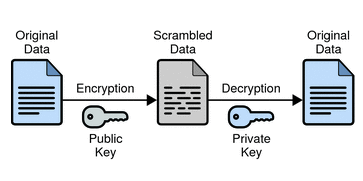
(Photo Credit: Oracle)
If a person tries to decode or decrypt your company data without a key, it will be virtually impossible if your key and encryption are strong. Attackers know this and, if determined enough, will sit and wait for a vulnerability or user error to just obtain the keys–leaving cryptography useless and your information visible. A security specialist will need to be well versed in cryptography when protecting company data.
Conclusion
With the increasing amount of data a company produces and the concerns that come with securing it, it’s easy to see why cybersecurity is becoming one of the fastest-growing industries. There is no discrimination in how or where attackers will illegally take their information, making cybersecurity not only a global concern but also a direct concern of an InfoSec practitioner. Businesses, and especially their information security specialists from every corner of the globe, need to be aware of the above threats and practice safe data protection measures in 2018.
Devin Morrissey prides himself on being a jack of all trades; his career trajectory is more a zigzag than an obvious trend, just the way he likes it. He pops up across the Pacific Northwest, though never in one place for long. You can follow him more reliably on Twitter.
This guest blog is part of a Channel Futures sponsorship.
You May Also Like
