One of the biggest challenges facing MSPs with regard to the cloud is the suspicion that customers have when it comes to placing their critical company data into a server that they do not directly control.
July 6, 2016
Sponsored Content
 This is Part 3 of our three-part series on how to offer great cloud services. In our first post here on MSPmentor, we asked, “Are you easy?” In that blog, we discussed how MSPs need to reduce the friction in the customer experience by automating processes. In our second post we asked, “Are you complete?” We discussed how to build stickier and more profitable cloud services using bundling, cross-selling and upselling as a way to reduce churn and increase average monthly revenue. In our last post of the series, we ask: “Are you secure?”
This is Part 3 of our three-part series on how to offer great cloud services. In our first post here on MSPmentor, we asked, “Are you easy?” In that blog, we discussed how MSPs need to reduce the friction in the customer experience by automating processes. In our second post we asked, “Are you complete?” We discussed how to build stickier and more profitable cloud services using bundling, cross-selling and upselling as a way to reduce churn and increase average monthly revenue. In our last post of the series, we ask: “Are you secure?”
One of the biggest challenges facing MSPs with regard to the cloud is the suspicion that customers have when it comes to placing their critical company data into a server that they do not directly control. Time and again, surveys of likely buyers and end users have pointed to security as the first concern when choosing a cloud services provider. While this concern is abating some in more recent data, it still easily outpaces price, support and quality as the top concerns when choosing an MSP.
Given the number of stories in the media of security breaches; rampant hacking and malicious attacks like ransomware; and government surveillance, it is not surprising that there is a perception that continues to slow the adoption of cloud services due to security.
For you as an MSP, there is only one way to combat these security concerns: Head on!
First, you need to have products that are actually secure–and it starts with your backup software. Second, you need to proactively inform your customers of your commitment to cloud security. Finally, it is important to remind customers of their existing security issues, which actually may be addressed in the cloud.
Then, ask yourself: “Am I secure?”
If you have not performed a security audit of your own systems, now is the time. Security audits include checking unnecessarily open ports on your servers, making sure you are offering the latest versions of your products, and checking the physical security of your own facilities. In fact, the biggest security hole at most cloud providers is the humble sticky note. Don’t be that company.
When we designed Acronis Backup Cloud, we wanted to ensure that we had the most secure solution that we could offer to MSPs. One of the primary ways we are able to offer high levels of security is by building the latest encryption features into our products. We offer up to 256-bit AES encryption, and the encryption applies to data both in transit and at rest. We also use top-tier data centers with biometric security and top security protocols. We also work very hard to adopt all of the compliance standards that our customers need.
And what about the fact that your customers likely have existing security issues that cloud may help address?
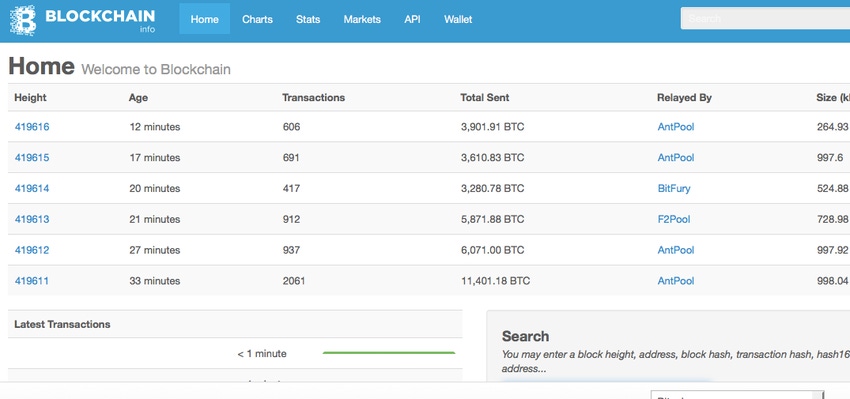
A good example of a new wave of technology to address this is Blockchain. This technology is already being widely used to secure crypto currencies like Bitcoin. Recently, Acronis announced that our products would be among the first in the data protection software industry to use these cutting-edge security features in backup and file sync and share applications–and across all solutions. Blockchain technology promises to deliver “tamper-proof” backups and storage. The groundbreaking Blockchain technology, which provides a record of digital events distributed across different participants or entities, has the potential to open up a broad range of new data protection use cases for businesses and organizations worldwide.
Acronis is taking a unique and targeted approach at how Blockchain can be used to solve specific data protection problems by seeking and developing use cases that exist today. Data and transactions that are protected from tampering by Blockchain can be used for those use cases where individuals or businesses absolutely must maintain the integrity of the original information.
For example, Acronis is currently extending its data storage solutions and file sync and share solutions with Blockchain technology to monitor data integrity and guarantee validity at all times. Examples of data that can be protected from tampering using Blockchain include property and medical records, stock transfers, chain-of-evidence for court documents, police video or security camera footage, long-term archiving that could be subject to IT audits, and “consortium” data storage, where multiple individuals or entities can securely store and exchange massive amounts of data and information.
Keep your cloud services secure today and in the future! Learn more about Acronis and Blockchain, and to try the prototype here. You can also tell us which use cases you see for data protection services that use Blockchain.
Jon McCarrick is Acronis Partner Technology Evangelist. Jon is a veteran in the cloud service provider space, having worked for Parallels and Open-xchange prior to joining Acronis. Jon’s mission is to create an active community of service providers around the Acronis product line. Expect to visit with Jon at your favorite trade show or find him on your favorite social media platform.
You May Also Like
