Ransomware is still a very real threat and has become even more targeted.
February 15, 2019
Sponsored by Webroot
Ransomware may have lost some of its malware market share throughout 2018, but threat actors are always thinking critically and creatively to find new ways to achieve their goals. As we move into the new year, ransomware is still a very real threat and has become even more targeted, using unsecured Remote Desktop Protocol (RDP) connections to deploy successfully.
Cybercriminals use tools like Shodan to scan for businesses that have not implemented adequate RDP security settings, leaving their environments open to infiltration by brute force tools. RDP access doesn’t require much knowledge to execute, and less sophisticated cybercriminals can buy access to already-hacked machines on the Dark Web. Once an organization has been breached by a criminal using RDP, it’s all over. Criminals can browse all data and hardware on the network, and map shared drives at their leisure to assess contents and value, and determine their attack strategy. This highly targeted approach significantly improves the chances of an organization paying the ransom, since criminals can effectively select the most valuable data to lock down.

www.fbi.gov/wanted/cyber/samsam-subjects
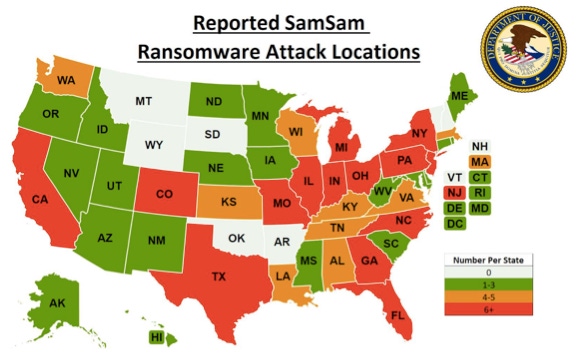
SamSam Criminals Indicted
As a quick recap: SamSam ransomware exploited RDP to effectively bring down entire cities (or portions of them, at least). You’ve likely seen news reports about it, since SamSam brought the city of Atlanta and the Colorado Department of Transportation to a grinding halt. This virulent threat affected numerous industries, including critical infrastructure, healthcare, transportation, and state and local governments.
The duo behind SamSam, Mohammad Mehdi Shah Mansouri and Faramarz Shahi Savandi, were wanted for allegedly launching the ransomware attack that encrypted hundreds of computer networks in the United States and other countries through the RDP attack vector. Since December 2015, Shah Mansouri and Shahi Savandi have received over $6 million USD in ransom payments from their victims. On Nov. 28, 2018, the U.S. Department of Justice announced charges against the two men.
www.justice.gov/opa/press-release/file/1114736/download
Even Cybercriminals Can’t Be Too Careful
Given the level of expertise it would’ve required to pull off so many successful attacks, it’s surprising that the SamSam creators got caught. It turns out their downfall was due to cryptocurrency payment systems. Although Bitcoin is arguably the best-known cryptocurrency exchange, numerous different types of cryptocurrency are available. Many cybercriminals choose to avoid Bitcoin, since the ledger system for this blockchain technology is public, meaning all the addresses to which victims sent ransom payments can be tracked. In this case, when Shah Mansouri and Shahi Savandi sent their Bitcoin to be cashed out to Iranian rial, the FBI could see that the specific ransoms they’d flagged had gone to an Iranian exchange Bitcoin address.

www.justice.gov/opa/press-release/file/1114741/download
Every cryptocurrency exchange that deals with Fiat money must follow Know Your Customer (KYC) regulations. That means the exchanges have identifiable information on their users. The FBI can then subpoena the exchange for this information to learn the identities of anyone who used specific Bitcoin addresses. In the case of the SamSam perpetrators, they didn’t change out their Bitcoin for another cryptocurrency with a private ledger system, such as Monero or Zcash. Private ledger cryptocurrencies allow users to move their funds without anyone tracking transaction details like sender and receiver address or payment amount. Such an oversight is how many cybercriminals have been caught. While this incident probably won’t be the last time a criminal leaves Bitcoin breadcrumbs behind, we expect the use of private ledger cryptocurrencies to grow significantly.
SamSam’s Gone, But RDP-delivered Payloads are Here to Stay
Although the SamSam creators are no longer running any campaigns, other ransomware variants like GandCrab and Crysis are upgrading their campaigns to include the RDP attack vector. Additionally, RDP compromise isn’t limited to ransomware; there are now multiple viable choices for payloads. Criminals can use RDP to gain access, then view all the hardware and choose the type of malware they believe will make the greatest impact and yield the highest profit. For example, if the CPU and GPU of a given system were high-powered, the criminal might decide they would deliver more profit by mining cryptocurrency, rather than waiting for the victim to pay a ransom.
How to Protect Businesses (Yours and Your Clients’) from RDP Attacks
Don’t use common TCP ports. Better yet, don’t open ports to the internet. Just use a whitelisted IP range for the local network.
Set maximum number of failed login attempts. This way, you can lock things down before a brute force attack can succeed.
Use a very secure password. Or, embrace two-factor authentication.
If you don’t use RDP, disable it! You’d be surprised how many people don’t even realize it’s enabled.
Use a premium service like VNC, TeamViewer or LogMeIn. That way, IT staff can provide remote assistance via an encrypted connection.
For additional information on unsecured RDP and the risks it poses to MSP clients, read our full blog post from July 2018.
Webroot is committed to protecting businesses from cyber threats through informative, educational content and comprehensive cybersecurity layers. Discover MSP-friendly, next-gen endpoint security that’s easy to manage and integrates with your favorite RMMs. Take a complimentary 30-day trial.
This guest blog is part of a Channel Futures sponsorship.
Read more about:
MSPsYou May Also Like
