Separating truth from fiction in cybercrime is anyone's guess. But some experts simply know more than others.
May 15, 2017
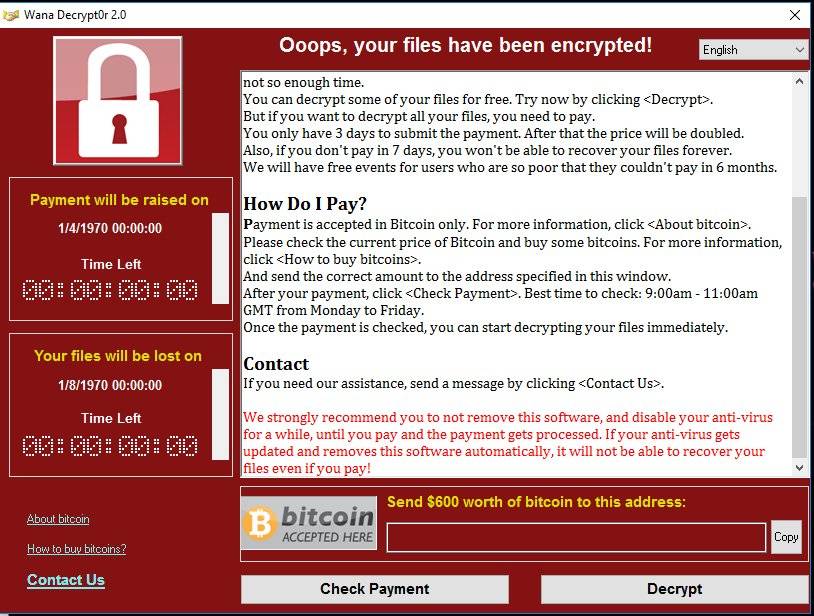
As the toll from the WannaCry ransomware attack mounts—150 countries, hundreds of thousands of organizations and systems counting—at least one security expert says much of the analysis of the event is wrong.
ZoneFox Head of Security Ian Trump says the WannaCry attack has all the hallmarks of a trial balloon and not the telltale signs of a bungled attack. What is more, the 22-year old “hero” who goes by the name of “MalwareTech” and who stumbled upon the way to stop the malware attack? He—or someone like him—was supposed to find that kill switch by design and turn it off, says Trump.
It’s not that Trump isn’t extremely grateful; he is. It’s just that in his world, Trump has come to realize that few things are ever what they appear to be.
Trump, of course, is the former Global Cyber Security Strategist with SolarWinds. This month, he joined ZoneFox, which is based in Edinburgh, U.K. The company was recently named as one of the country’s most promising startups. For background, Trump served with the Canadian Forces (CF), Military Intelligence Branch, and has held high positions in the industry for more than a decade. He’s also contributed to SC Magazine, Infosecurity, CBR, The Times, USA Today, The Sunday Herald and other other publications.
I last sat down with him for an interview in March. Then Trump expressed some bit of optimism on the cybersecurity front. Over the weekend we spoke by phone. His disposition was decidedly different. This episode makes vendors, governments and customers alike all look bad, Trump says, especially after the NSA tool known as Double Pulsar was leaked publicly.
“I feel that the ball was dropped here by everybody in the cybersecurity business, from operations who should have been blocking the two ports on the firewall that could have prevented this thing, to the anti-virus companies for not issuing either multiple signatures or putting in the heuristic detection of the exploitation of the protocol, and finally, to the government agencies that are supposed to be warning us about impending doom,” Trump says. “It’s kinda like an asteroid hit the planet and everybody is standing around the crater say ‘yeah, that was pretty f***ing bad.’”
Who Is behind the attack? And why do you think it is a trial balloon?
Trump says the Russians have fingerprints all over this, which is curious, I thought, given that most of the entities impacted were Russian. Trump brushed that aside.
“Let’s be clear, the Russians have an absolute history of using their own people with a cavalier consideration to their own health and welfare,” he says. “So testing your own national infrastructure in this kind of heinous attack, to me, totally goes to the Russian mentality. They want to be ready for when the NSA launches something on them.”
Trump concedes he is pushing the envelope with his opinion. But he believes whomever is behind the attack is deliberately making a statement.
“We just saw the mother of all bombs dropped… maybe this is the mother of all cyberattacks as a demonstration?” he says.

Ian Trump, ZoneFox
So why target the UK’s National Health Care System?
“To use a military term, I think it was a ‘reconnaissance in force.’ They shot something over there to see what would come back at them and they went, ‘holy crap this was really successful,’” says Trump. “I think they put up the trial balloon to see what kind of damage they could do to a country’s national infrastructure.”
But don’t nation-states still see this as an act of war?
“I completely agree with you… In terms of scope, this was the functional equivalent of flattening a hospital in Kunduz, Syria. The difficulty is when you look up at the sky, you do not see the markings of any nation in this particular attack. Even if you could pinpoint ‘these guys,’ a government can disavow any knowledge of what happened. This is the biggest problem we have in cyber,” says Trump. “Was the NHS caught with their pants down? Absolutely. But can they point the finger at who did that? The can’t with any degree of certainty… The adversary will burn the infrastructure… In five or six years they will get caught at some time. But now? It just cannot be done at this point because there are so many things we still don’t know. Was this a genie that got out of bottle? Was this a deliberate attack? No one knows what the mindset of the protagonist was yet. What were they trying to achieve? It kinda looks like a ransomware attack and the press is going to report that… but the immediate response now is this was an example of when you hook up important things to an unreliable infrastructure.”
Cyber capabilities among nations differ greatly. Coordination and execution, too. How do we know that the attack was officially sanctioned versus some guys going rogue?
“[We don’t.] Patriots aren’t necessarily just Americans. Everybody can be patriotic for their country. The desire, though, to make a shit-ton of money in countries that aren’t rewarding people for the skill that they bring to their nation-state or because the economies of scale can’t fulfill their dreams of prosperity—that’s when you get guys that are nation state-actor trained who get together with their friends and get a case of vodka and sit down and say ‘you know what? I love my country but I’m not compensated enough for what I am doing for them and I have skills that are easily translated into a criminal enterprise,’” Trump says.
“We use bug-bounty programs to try and persuade people that are trained in the art of vulnerability discovery and reverse engineering to use these economic incentives and not go criminal with what they have discovered. I would say we are relatively successful but the problem is it is never enough.”
Why do you believe the so-called ‘kill switch’ was put there on purpose expressly to be found?
“Imagine if it was an unknown zero-day—something that there wasn’t the vendor patch issued for it in March? Imagine if the payload was destructive and not just ransomware?” he says.
“When I put my hat on and starting thinking what it means, I think we have started down the path of test cyberwar. We hope we will never get there because we just learned [about] what a moderate attack can do. The big smoking gun for me that means that this was not a normal cybercriminal attack was the kill switch. If I were a cybercriminal, I would monetize the shit out of this thing that I just built because I have an entire affiliate marketing program build around it… [With the kill switch], this feels more like a test balloon than an actual, overt cybercrime… Who puts an off switch into their awesome money-making machine? This was a slot machine for Bitcoin.”
What lessons have we learned?
As for those who failed to protect their own organization or a customer’s, Trump has little sympathy. People in the security community were aware of new malware threats and patches, and had sufficient time to respond. Those who did nothing, he says, “might be better off working for Cirque du Soleil instead of IT.”
About the Author(s)
You May Also Like


