Ransomware Warning on Windows 10 Download Ruse
Security specialists are warning Windows 10 downloaders not to be duped by a faked email purporting to come from Microsoft but instead housing an attachment containing the nasty CTB-Locker ransomware.
Security specialists are warning Windows 10 downloaders not to be duped by a faked email purporting to come from Microsoft (MSFT) but instead housing an attachment containing the nasty CTB-Locker ransomware.
Cisco’s (CSCO) Talos security team noticed a new malware campaign to distribute the CTB-Locker ransomware posing as an email update from Microsoft to inform users that their Windows 10 download is ready. But, in fact, it’s a ransomware ruse traced back to a Thailand IP address.
“Adversaries are always trying to take advantage of current events to lure users into executing their malicious payload,” Talos wrote in a blog post. “This threat actor is impersonating Microsoft in an attempt to exploit their user base for monetary gain. The fact that users have to virtually wait in line to receive this update, makes them even more likely to fall victim to this campaign.”
The email is similar to one that Microsoft sends to users pre-registering for the Windows 10 upgrade but there are some telling text and other mistakes that users can recognize once informed. As Talos describes the malicious email, the “From” address appears to come from Microsoft but a look at the email header reveals that it originates from an IP address in Thailand.
And, while the attackers deploy a color scheme in the email similar to one Microsoft uses, the text and character errors stand out on closer inspection, Talos said. To try to trick readers into believing the email is authentic, the attackers add a link reference that the email has passed a malware inspection and a disclaimer that looks like it would come from Microsoft.
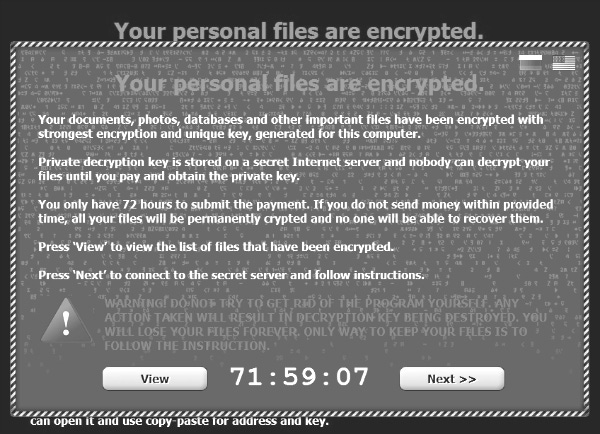
However, “once a user moves past the email, downloads the zip file, extracts it, and runs the executable, they are greeted with a message” telling them their personal files are encrypted with CTB-Locker, demanding payment within 96 hours for an encryption key or their files will be permanently encrypted with no chance for recovery.
What’s happened is a 734KB attachment used in the emails containing the ransomware has been unleashed to encrypt documents, media files and other materials.
“The payload is CTB-Locker, a ransomware variant,” Talos wrote. “Currently, Talos is detecting the ransomware being delivered to users at a high rate.”
This variant of CTB-Locker is unusual in a few ways, reported the U.K.’s Register. While it asks its victims to pay in Bitcoin, the 96-hour window allotted is shorter than most malware demands.
But, in perhaps the most unusual of twists in ransomware cases, the cyber kidnappers show their victims a list of encrypted files and offer to decrypt five for free.
“If you look at malware like Cryptolocker, it has built a market for itself because people know that if they pay they will get their files back,” Craig Williams, Cisco Talos security outreach manager, told the Register.
“CTB-Locker is doing the same thing by proving to people they can do what they say they can do,” he said.
“If you pay the attacker in Bitcoin then it’s a very smooth funding stream; the money goes directly to paying the [malware] development team,” he said. “That’s why we’re seeing such a fast development cycle in ransomware.”
Security expert Stu Sjouwerman advised users to “be very careful with any email claiming to be from Microsoft about ‘your Windows 10 Upgrade.’ Make sure that any links in the email really go to Microsoft. Better yet, do not click on any link or open any attachment, but go to the Microsoft website for more information.”
About the Author(s)
You May Also Like


