Many endpoint protection solutions have been updated to detect Locky ransomware but as a new variant, emails containing the IKARUSdilapidated strain can be designated as “unknown file” types and slip through security tools.
A massive, worldwide ransomware attack is currently unfolding, powered from more than 11,625 distinct IP addresses in 133 different countries, experts at cyber security vendor Comodo said today.
The campaign was first detected on Aug. 9, and more than 62,000 phishing emails related to the attack were detected at Comodo-protected endpoints alone, as of Friday.
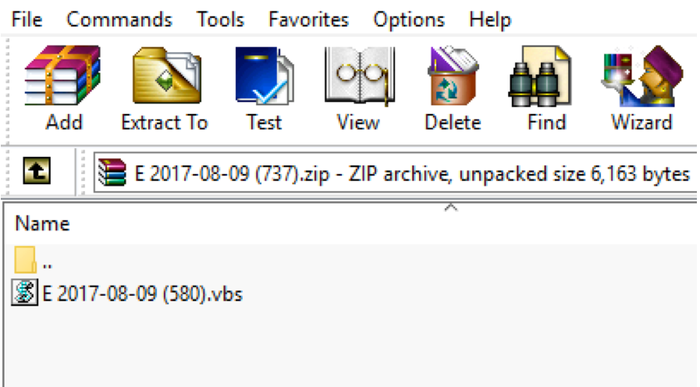
Emails use social engineering to induce users into opening a docx, pdf, jpg, zip or other file containing the ransomware, dubbed “IKARUSdilapidated,” after a phrase that appears in the code string.
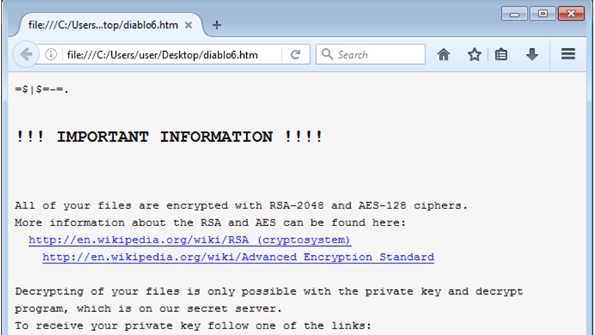
“If the user does as instructed, the macros then save and run a binary file that downloads the actual encryption Trojan, which will encrypt all files that match particular extensions (including the common ones on most machines),” Comodo researchers wrote in a report that was provided to MSPmentor in draft form, because it is still being completed. “Filenames are converted to a unique 16 letter and number combination with the .locky file extension.”
Read the Draft Report: ‘IKARUSdilapidated’ Ransomware Attack
Locky is a very common type of ransomware that emerged in 2016 and has been used in a wide range of cyber attacks since.
“The attachment is an archive file, with the name ‘E 2017-08-09 (580).vbs’ where 580 is a number changing for each email and vbs is an extension which varies as well,” the report says.
Many endpoint protection solutions have been updated to detect Locky ransomware but as a new variant, emails containing IKARUSdilapidated can be designated as “unknown file” types and slip through security tools.
After the files are encrypted, users are given instructions for downloading a Tor browser and directed to a site on the dark web where the cyber criminals demand a ransom payment of one half to 1 bitcoin.
As of today, 1 bitcoin was valued at $4,369.27.
The top five countries of origin for the IP addresses being used by the attackers are Vietnam, India, Mexico, Turkey and Indonesia.
“When the team checked the IP range owners, we see that most of them are telecom companies and ISPs,” the Comodo draft report said.
“This tells us the IP addresses belong to infected, now compromised computers (also called “zombie computers”),” the report continues. “This quantity of servers can only be used for a specific task if they are formed into a large bot network (or botnet), and have a sophisticated command and control server architecture.”
Comodo experts recommend adopting a “default deny” security posture, which calls for blocking all unknown files from an IT infrastructure until they’re verified as safe.
Send tips and news to [email protected].
About the Author(s)
You May Also Like


